VoLTE and IMS Security for Service Providers
INCLUDED IN THIS USE CASE
BIG-IP
Diameter Traffic Management
DDoS Protection Solutions
Carrier-Grade NAT Solutions
The Challenge
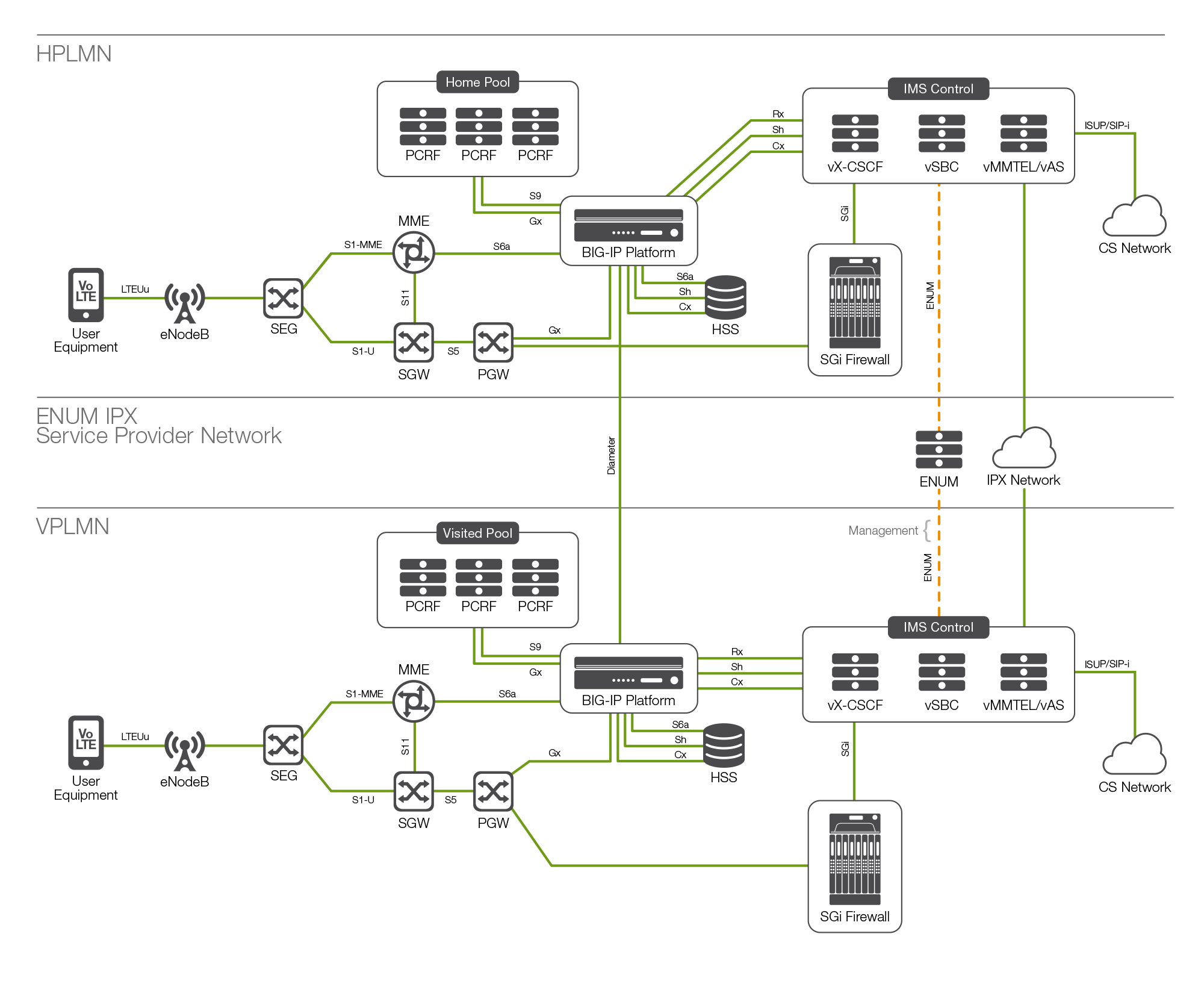
VoLTE is crucial for service providers, consolidating voice traffic from circuit switch networks to all-IP LTE networks, thereby reducing overall network operation costs.
As the rate of VoLTE adoption rapidly increases, attacks against the signaling resources used to provide services to customers—including real-time signaling protocols—will also increase. As a result, VoLTE security—which focuses on protecting and controlling signaling protocols, including Diameter and SIP—is becoming more critical.
With more and more devices coming to market with support for IPv6 only, the ability to manage and control potential signaling spikes caused by IPv6 devices is equally important. When a SIP signaling storm happens because of unintended actions, other node outages in the network, or malicious attacks, it’s important to rate-limit SIP requests to the Proxy-Call Session Control Function (P-CSCF) so that it’s not overwhelmed.
Plus, the increase in the types and numbers of new devices comes with massive and ongoing changes in traffic and usage characteristics. To handle all these changes, operators require solutions which are capable of very high connection rates and increasing concurrency.
An important IMS trend is the rise of Rich Communications Services (RCS), the protocol that will replace SMS. It was formed in 2007 by a group of industry players and in 2008 was embraced by the GSM Association. However, disappointing carrier participation and other factors kept it from gaining any real traction. Google announced in early 2018 that it had been working with every major mobile service provider in the world to adopt the RCS protocol. RCS combines the best of Facebook Messenger, iMessage, and WhatsApp into one platform. The result is Chat, a protocol based on RCS Universal Profile which will supersede SMS.
The Solution
The F5 BIG-IP platform helps ensure VoLTE service continuity and protects against unauthorized access, unexpected traffic peaks, signaling storms, session spoofing, and privacy attacks.
The F5 firewall solution, along with the SIP Application Layer Gateway (ALG), monitors SIP messages and only permits user data streams when the SIP ALG validates the SIP control channel, providing security for user traffic in the network. By combining firewall, traffic management, distributed denial-of-service (DDOS) protection, carrier-grade network address translation (CGNAT), and rich protocol support (SIP, Diameter, HTTP, DNS, ENUM, and others), the BIG-IP platform can enforce controls on the S/Gi LAN, directly in front of the P-CSCF and other application servers, and on roaming interconnect points. F5 solutions can secure and distribute traffic, regardless of whether that traffic is from IPv4 or IPv6 devices.
By doing so, F5 solutions combine security and availability functionalities to maintain network service during times of unexpected stress. Additionally, these solutions enable service delivery with the highest possible protection, connection rates, and concurrency levels in the industry—more than a terabit of throughput and up to 1.2 billion concurrent connections.
F5 helps you:
- Deliver fast and secure VoLTE and IMS services.
- Provide the highest possible security protection.
- Support high connection rates and a high level of concurrency.
- Protect your brand and maximize subscriber quality of experience (QoE).