Bot Management Solutions
Protect your website, mobile apps, and APIs from malicious bots while maintaining access for the good bots that help your business.
What is Bot Management?
Bot management is part of a comprehensive security strategy to optimize customer engagement, protect digital assets, and prevent online fraud.
Bots make the Internet work—from search engine crawlers that bring the world to your fingertips to chatbots that engage and influence your customers early in the buyer’s journey.
Bots also scale automated attacks like credential stuffing, which can result in account takeover (ATO) and fraud. Motivated cybercriminals leverage a sophisticated arsenal of bots, automation, and evasion techniques. They also perform ongoing reconnaissance to identify security countermeasures and constantly retool their attacks to evade detection.
Don’t settle for bot management that fails to deter cybercriminals or frustrates customers with friction that leads to transaction abandonment, lost revenue, and hot leads for your competitors.
Learn about the new era of automated fraud.
Get the eBook ›
Fake Accounts
Bad actors use fake accounts to commit financially motivated attacks, including reward abuse on retail sites, money laundering via online banking, and even as a disguise for credential stuffing.
Account Takeover
Testing of large numbers of compromised credentials (i.e., usernames and passwords breached from another site) by attackers against your login application to compromise those accounts for monetary gain.
Carding Fraud
The automated abuse of checkout pages to identify missing values of credit cards like expiration date or card security code (CSC).
Inventory Hoarding
Acquisition of goods or services by abusing the application in a manner that a normal user would be unable to undertake manually, eroding customer trust.
Gift Card Cracking
A type of brute force attack in which attackers check millions of gift card number variations on a gift card application to identify card numbers that hold value.
Content Scraping
The use of automated tools to collect large amounts of data from a target application in order to reuse or sell that data elsewhere.
Marketing Fraud
Automated repeated clicking or requesting or submitting content, skewing app-generated business intelligence data.
Why Bot Management Matters
Fraud is increasing in sophistication and is often driven by financially motivated organized crime rings that employ bots to carry out their attacks. These groups are also known for retooling their attacks to overcome commoditized bot protection, which puts security teams on the defensive and strains precious resources. Failing to effectively manage bots can have big impacts on your application performance, your customer experience, and your business.
How F5 Can Help
Security must adapt to attackers that retool to bypass countermeasures—without frustrating users.
This ability to react as apps and attackers adapt can dramatically improve business outcomes by slashing fraud losses, providing better customer experiences, and maximizing operational efficiencies and business intelligence.
Explore F5 Bot Management Solutions
Stop Automated Attacks


The economics are in the hacker’s favor
Apps are the business. Automation enables organizations to be first to market, first to profit, and first to innovation with apps that literally change the world.
Conversely, attackers have embraced bots and automation to carry out their attacks, leading to abuse, account takeovers, fraud, and damaged brands.
Shape Enterprise Defense
Deliver dedicated, outcome-driven defenses to protect your most critical assets from sophisticated cybercriminals.
Silverline Shape Defense
Gain advanced protection against credential stuffing and automated fraud in a convenient managed service.
Prevent Automated Fraud


Security that reacts as attackers adapt
The most sophisticated attackers will retool against all countermeasures, using techniques that emulate human behavior to evade detection. Security must maintain resilience and effectiveness to protect businesses from cybercrime that can lead to unauthorized access, account takeover, and fraud.
Shape Enterprise Defense
Get the solution that distinguishes good from bad actors, invisibly protecting every app from attack, fraud, and abuse.
Silverline Shape Defense
Prevent large-scale fraud with an advanced solution that delivers continuous protection—even when attackers retool.
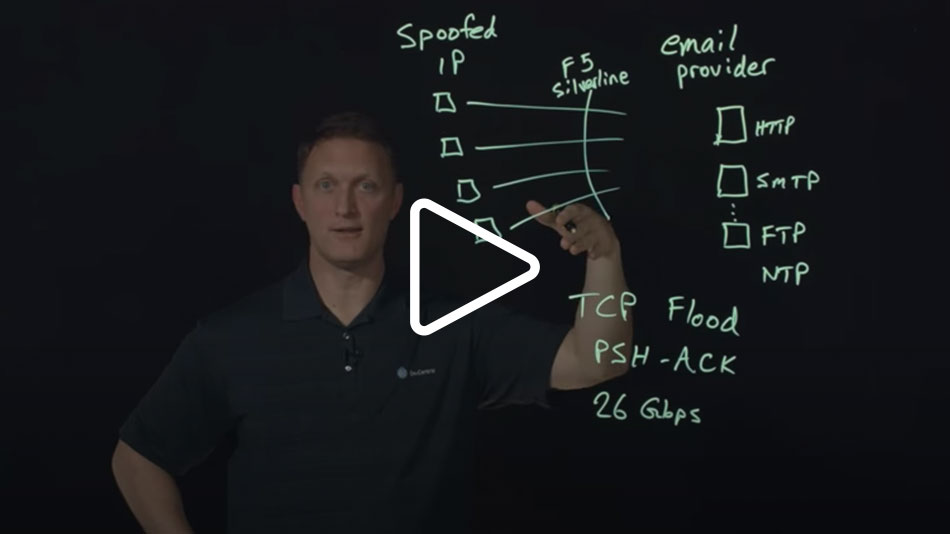
Protect Against DDoS Attacks


Industry-leading DDoS detection and mitigation
Distributed denial-of-service (DDoS) attacks threaten businesses with downtime that can damage their brand and even lead to financial losses. F5 provides DDoS protection that makes sense for your architecture.
Under attack? Call (866) 329-4253 or +1 (206) 272-7969
Silverline DDoS Protection
Provides fully managed, cloud-based protection that detects and mitigates large-scale SSL/TLS and application-targeted attacks in real time.
Network Firewall
Protects against attacks that consume network and application resources and can signal upstream to the cloud-scrubbing service.
F5 Advanced Web Application Firewall (WAF)
Defends against layer 7 application attacks that target CPU or memory resources and can signal upstream to the cloud-scrubbing service.
Ecosystem Integrations


How do F5 solutions integrate with bot and abuse ecosystems?
F5 collaborates with the world’s leading tech companies to create joint solutions that protect the most valuable brands from bots, abuse, and fraud.
Protect Logon and Digital Touchpoints
Accelerating easy, highly secure access with Shape and Okta
Secure Customer Identity and Account Management
Protecting SAP Customer Data Cloud with Shape Security
Defend Your Salesforce Commerce Cloud Applications
Protecting and mitigating real-time bot traffic with F5 Bot Defense
Resources
ON-DEMAND WEBINAR
Defeat Bot Attacks with New Silverline Shape Defense Managed Service